Responding to a data breach: Free checklist
Responding to a data breach checklist
Data breaches can have serious consequences for businesses, from financial loss to reputational damage. This checklist helps guide organizations through the steps required to respond effectively to a data breach. It covers everything from verifying the breach, containing it, notifying affected parties, and improving security practices to prevent future incidents.
Using this checklist will help ensure your organization handles the breach professionally, minimizing risk and ensuring compliance with legal requirements.
How to use this responding to a data breach checklist
To ensure your organization manages a data breach effectively, use this checklist as a step-by-step guide. Here’s how to maximize its benefits:
- Follow each step carefully: This checklist is structured to cover every stage of the breach response. Start by verifying the breach, containing it, and notifying relevant parties. Continue through to the final post-breach review to assess security measures. Moving through the checklist in order ensures that no critical steps are missed, from legal obligations to internal processes.
- Involve all necessary departments: A data breach response requires collaboration across multiple teams. Involve your IT department to handle technical issues, legal counsel to manage compliance, PR for external communication, and HR for internal updates. Coordinating these departments ensures a unified, comprehensive response.
- Document every action: Keep a detailed log of all actions taken during the breach response. This documentation will be essential for any legal or regulatory inquiries, and it helps you track how the breach was handled at each step. Accurate records also provide valuable insights for refining your future incident response processes.
- Tailor it to your organization: While the checklist provides general guidelines, adjust it to fit your business’s specific needs. Different industries have unique legal and operational requirements, so make sure your response plan aligns with relevant laws and internal policies.
- Update regularly: Data breach risks and regulations evolve. Review and update this checklist periodically to ensure it remains relevant to new threats, technologies, and compliance requirements.
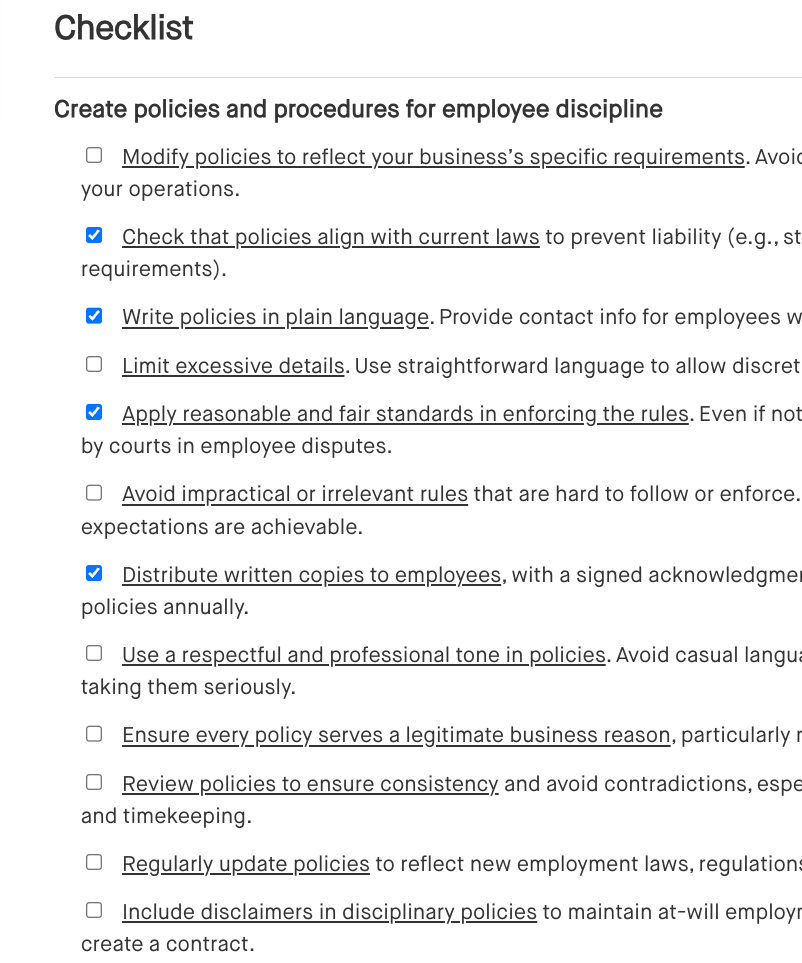
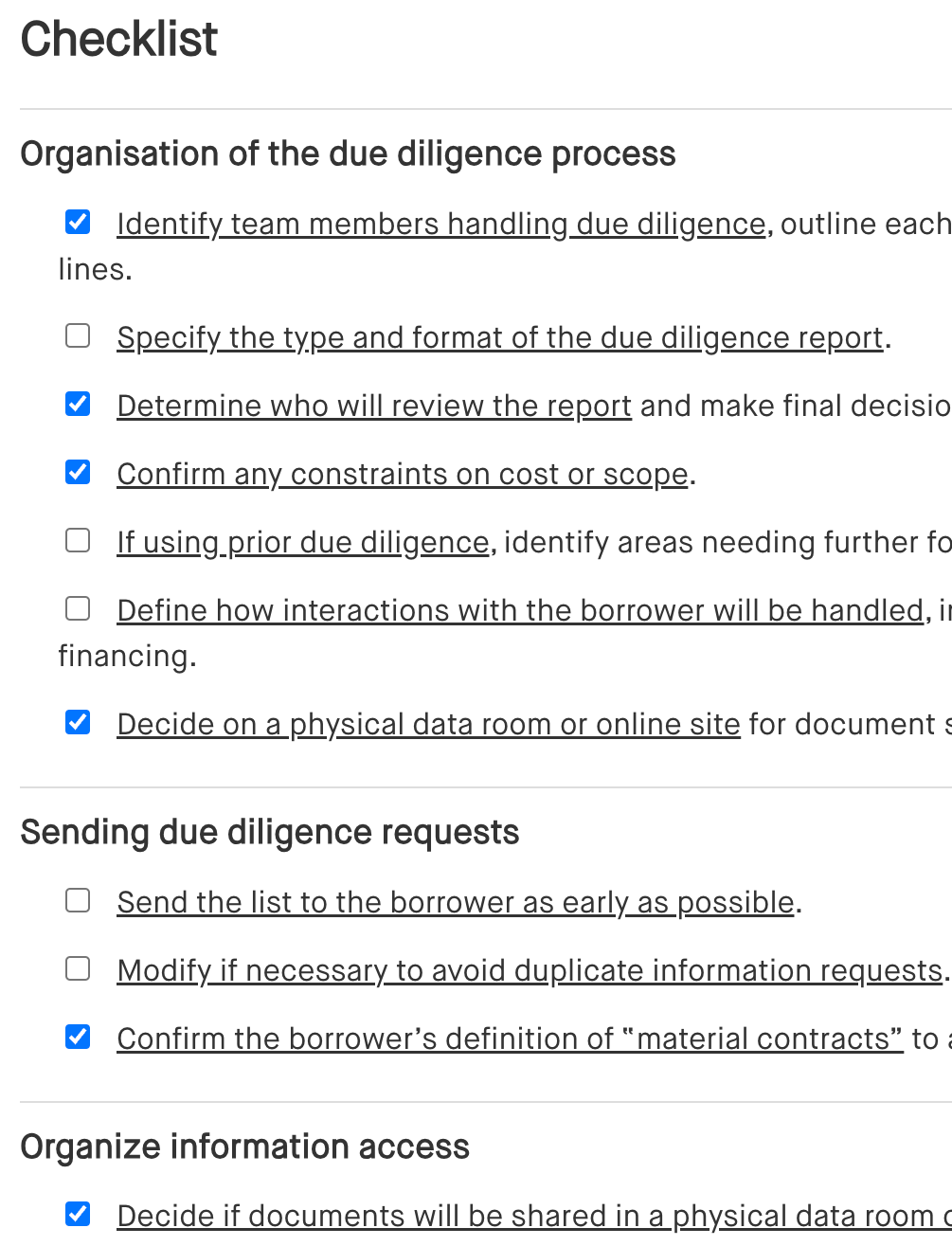
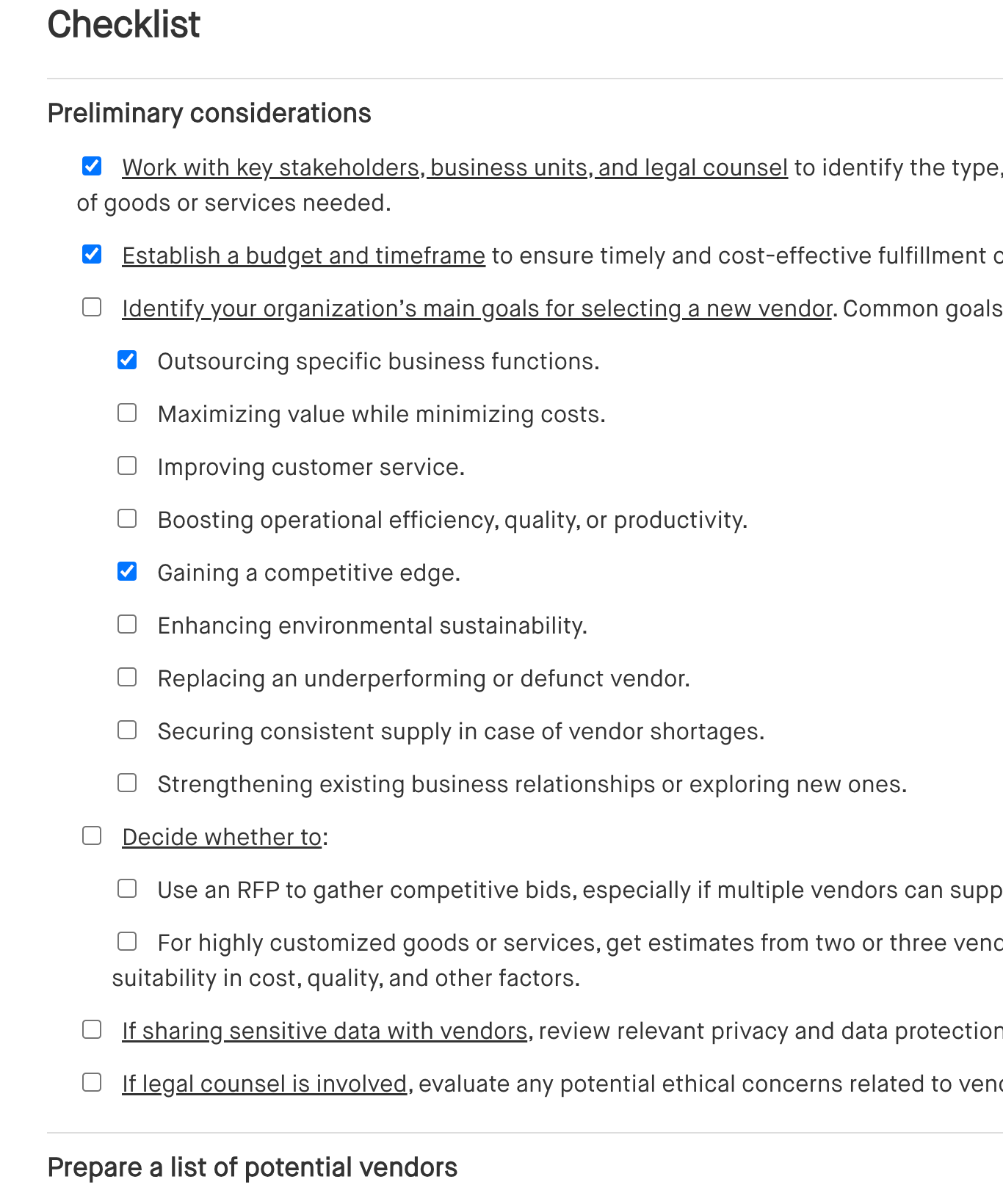
Checklist
Benefits of using a responding to a data breach checklist
A responding to a data breach checklist offers multiple advantages, ensuring that your organization manages the breach effectively and complies with legal requirements. Here’s how it helps:
- Ensure compliance with legal obligations: The checklist helps you stay aligned with federal, state, and industry-specific laws, reducing the risk of penalties or legal actions. It guides you through the necessary steps to meet notification requirements, regulatory disclosures, and data protection laws like GDPR or HIPAA.
- Streamline your response process: A structured checklist helps you act quickly and systematically in the event of a data breach, minimizing chaos and ensuring that all critical steps are covered. This not only reduces the impact of the breach but also helps limit further damage to your systems and reputation.
- Minimize business disruption: By following the checklist, you can ensure that your response team contains the breach and mitigates its effects without major interruptions to business operations. The clear instructions make it easier to focus on containment and remediation.
- Protect your reputation: The checklist helps you manage communication with affected parties, media, regulators, and law enforcement in a timely and professional manner. This transparency and quick response can help preserve trust with customers, partners, and stakeholders.
- Prepare for future incidents: Documenting your response allows you to learn from each breach. The checklist provides a solid foundation for post-breach analysis, helping you strengthen your cybersecurity program and be better prepared for future incidents.
Frequently asked questions (FAQs)
Q: Why do I need a data breach checklist?
A: A data breach checklist provides a clear, step-by-step guide to managing breaches, ensuring that you meet legal requirements, mitigate further damage, and protect your organization’s reputation. It simplifies a highly complex process, so you don’t overlook any critical steps during a stressful situation.
Q: Who should use this checklist?
A: This checklist is useful for IT security teams, data breach response teams, legal counsel, HR, and any staff members responsible for handling sensitive data or responding to security incidents.
Q: What should I do if I discover a data breach?
A: Start by verifying the breach and assessing its impact. Then, follow the checklist to contain the breach, notify the appropriate parties, and initiate an internal investigation. Ensure you document every action and communicate with key stakeholders.
Q: How does this checklist help with legal compliance?
A: It ensures that you follow federal, state, and industry-specific regulations, including mandatory notification to affected individuals, regulators, or law enforcement. By using the checklist, you reduce the risk of fines and lawsuits associated with non-compliance.
Q: How often should I update the checklist?
A: It’s advisable to review and update your data breach checklist regularly—at least annually—or whenever new regulations, technologies, or threats emerge. Keeping it up to date ensures your response remains effective and legally compliant.
Q: Should I engage external help during a data breach?
A: Depending on the severity of the breach, you may need external assistance, such as engaging a forensic team, outside legal counsel, or specialized consultants. The checklist prompts you to evaluate this need early in the response process.
Q: What should I communicate to affected individuals?
A: Your communication should include a clear explanation of what happened, what data was affected, what actions your organization is taking to resolve the issue, and any steps individuals can take to protect themselves. The checklist guides you through preparing these communications.
This article contains general legal information and does not contain legal advice. Cobrief is not a law firm or a substitute for an attorney or law firm. The law is complex and changes often. For legal advice, please ask a lawyer.